Following on from my last post discussing micro segmentation within an Azure secured hub, I will now cover deploying internet facing resources, including app gateways, into the same secured VWAN hub architecture.
When deploying an application gateway into a secured hub connected spoke vnet, we are faced with a dilemma – the app gateway must exist within the secured hub peered vnet in order to access its back ends, however, it cannot have its internet bound traffic secured and thus routed via the firewall.
Why is that configuration not possible? Well – asymmetric routing. Let me explain…
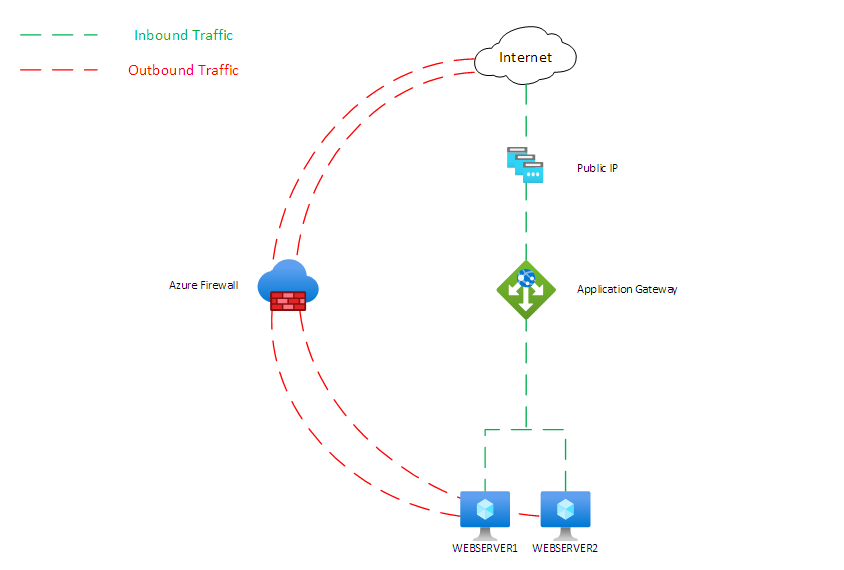
In the below diagram, of an example internet facing service, you will see that traffic enters via a public IP attached directly to the application gateway.
However, return traffic is forced via the Azure firewall due to the secured hub configuration to secure internet traffic, meaning default route is advertised to the app gateway with a next hop of the Azure firewall.
In practice, this means internet traffic enters one way (directly) and exits another (via the Azure firewall) causing asymmetric routing and the app gateway to not function.
So, how can we fix this?
The answer is to “remove internet traffic security” on the vnet containing your directly internet facing resources (e.g app gateways). This can be done by visiting Firewall Manager -> Virtual Hubs -> Selecting your virtual hub -> Security Configuration.
This should then take you to the following screen –
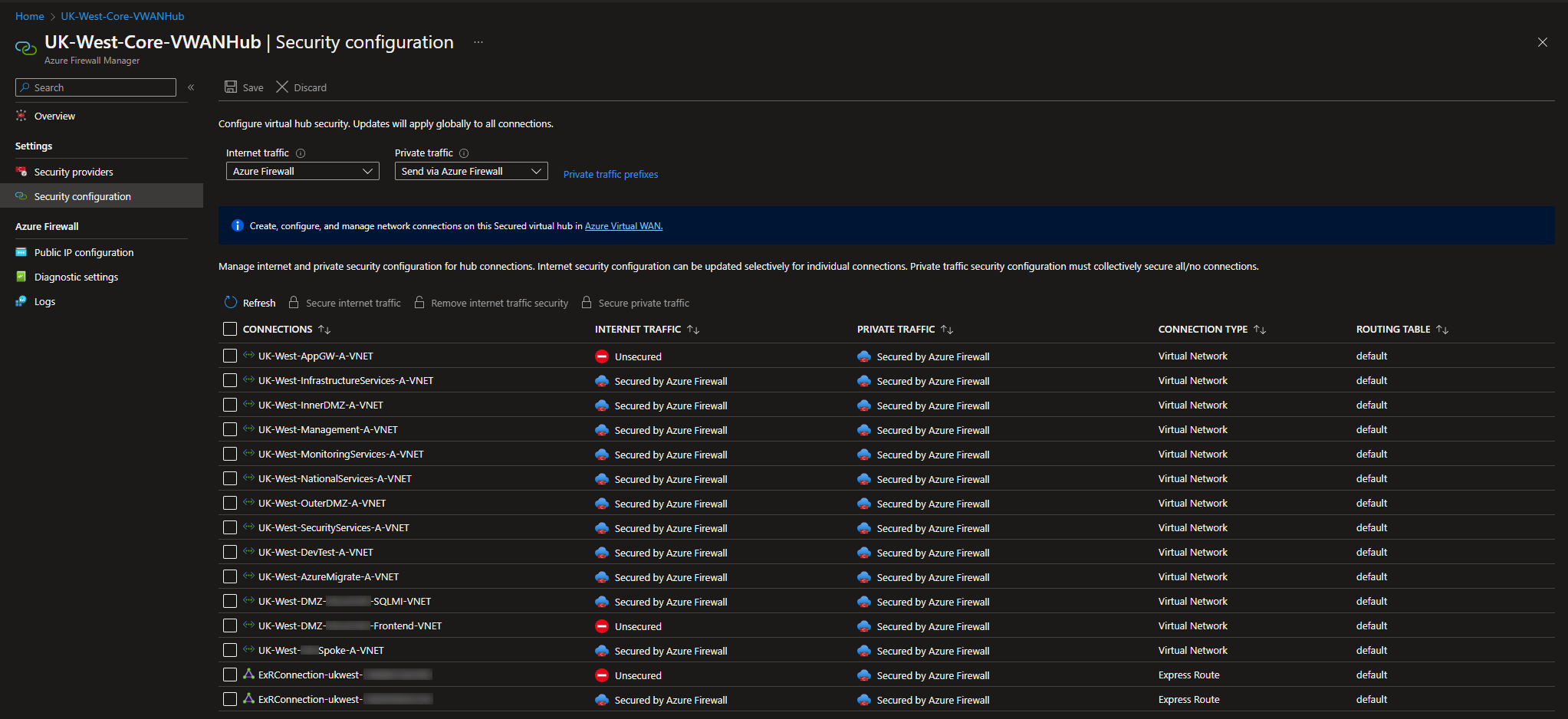
From here you can select the vnet containing your application gateway and click the “Remove internet traffic security” button.
This will “unsecure” the internet bound traffic, effectively stopping the advertisement of default route to that vnet with a next hop of the Azure firewall and allowing internet traffic to go direct.
NOTE: All of the above also applies not only to application gateways but also any other directly internet facing resources, for example – if VMs were deployed running a Netscaler image to serve internet facing websites, the vnet the Netscaler VMs lived in would need to have its internet traffic “unsecured”.
Good luck!