Azure Automation Runbook RBAC Delegation
Runbooks in Azure Automation accounts live in a shared space with no per-runbook access control through the portal. If you need to let a team manage their own runbooks without giving them access to the whole automation account, the only way is to assign roles directly on the runbook resource — which isn't exposed in the UI.
This script handles that through the Azure REST API.
The Script
The script supports three modes: view (list assignments), set (assign a role), and delete (remove a role).
param(
[Parameter(Mandatory)] [string] $Mode, # view | set | delete
[Parameter(Mandatory)] [string] $SubId,
[Parameter(Mandatory)] [string] $RG,
[Parameter(Mandatory)] [string] $AutomationAccount,
[Parameter(Mandatory)] [string] $RunbookName,
[string] $UserOrGroup, # email address or object ID
[string] $RoleName # e.g. "Contributor", "Reader"
)
$scope = "/subscriptions/$SubId/resourcegroups/$RG" +
"/Providers/Microsoft.Automation/automationAccounts/$AutomationAccount" +
"/runbooks/$RunbookName"
if ($Mode -eq "view") {
Get-AzRoleAssignment -Scope $scope
}
if ($Mode -eq "set") {
# Resolve email to object ID if needed
$objectId = $UserOrGroup
if ($UserOrGroup -match "@") {
$objectId = (Get-AzADUser -UserPrincipalName $UserOrGroup).Id
if (-not $objectId) {
$objectId = (Get-AzADGroup -DisplayName $UserOrGroup).Id
}
}
New-AzRoleAssignment -ObjectId $objectId -RoleDefinitionName $RoleName -Scope $scope
}
if ($Mode -eq "delete") {
if ($UserOrGroup -eq "*") {
Get-AzRoleAssignment -Scope $scope | Remove-AzRoleAssignment
} else {
$objectId = $UserOrGroup
if ($UserOrGroup -match "@") {
$objectId = (Get-AzADUser -UserPrincipalName $UserOrGroup).Id
}
Remove-AzRoleAssignment -ObjectId $objectId -RoleDefinitionName $RoleName -Scope $scope
}
}Usage Examples
View all role assignments on a runbook:
.\Set-RunbookRBAC.ps1 -Mode view `
-SubId "00000000-0000-0000-0000-000000000000" `
-RG "my-rg" `
-AutomationAccount "my-automation" `
-RunbookName "Start-VMs"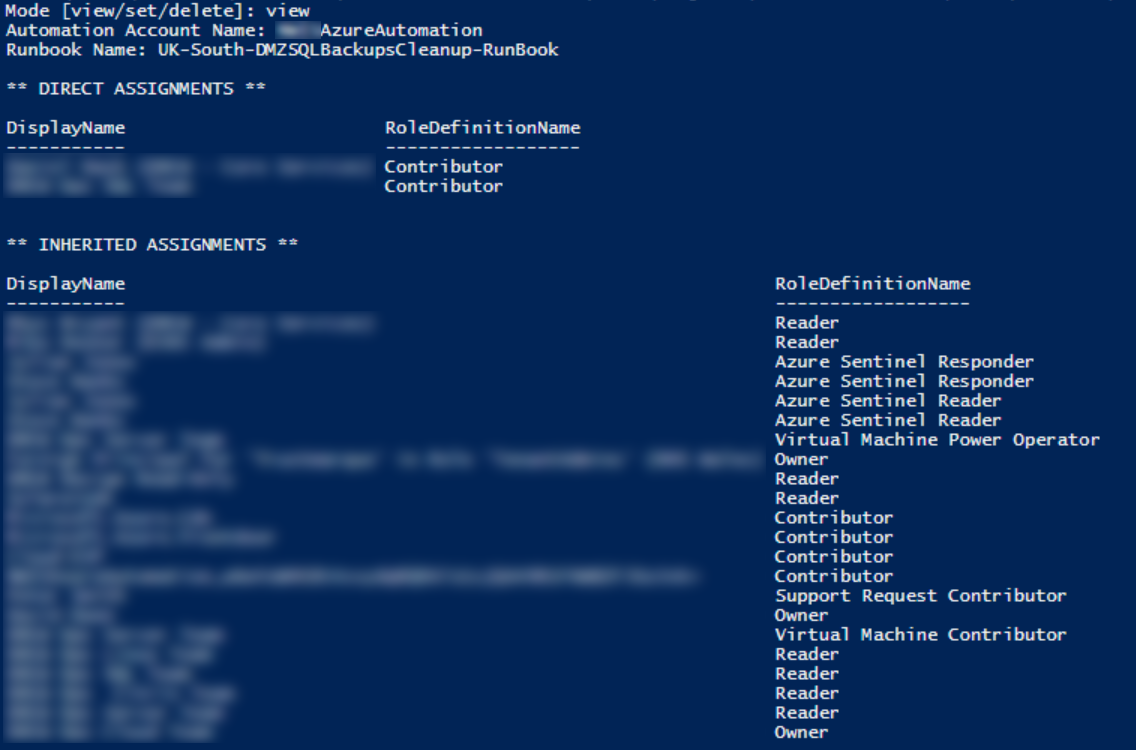
Grant a team Contributor access to a specific runbook:
.\Set-RunbookRBAC.ps1 -Mode set `
-SubId "00000000-0000-0000-0000-000000000000" `
-RG "my-rg" `
-AutomationAccount "my-automation" `
-RunbookName "Start-VMs" `
-UserOrGroup "teamlead@company.com" `
-RoleName "Contributor"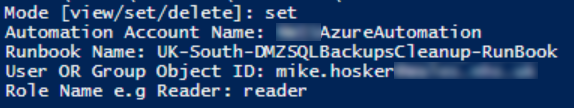
Remove all assignments from a runbook:
.\Set-RunbookRBAC.ps1 -Mode delete `
-SubId "00000000-0000-0000-0000-000000000000" `
-RG "my-rg" `
-AutomationAccount "my-automation" `
-RunbookName "Start-VMs" `
-UserOrGroup "*"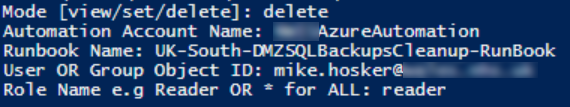
Note on Scope
Role assignments made at the runbook resource scope are in addition to any inherited permissions from parent scopes (resource group, subscription). A user with subscription-level Contributor will still have access regardless of runbook-level assignments — this approach is for granting additional scoped permissions, not for restricting broader ones.