When using Internet Explorer you may encounter the following page:
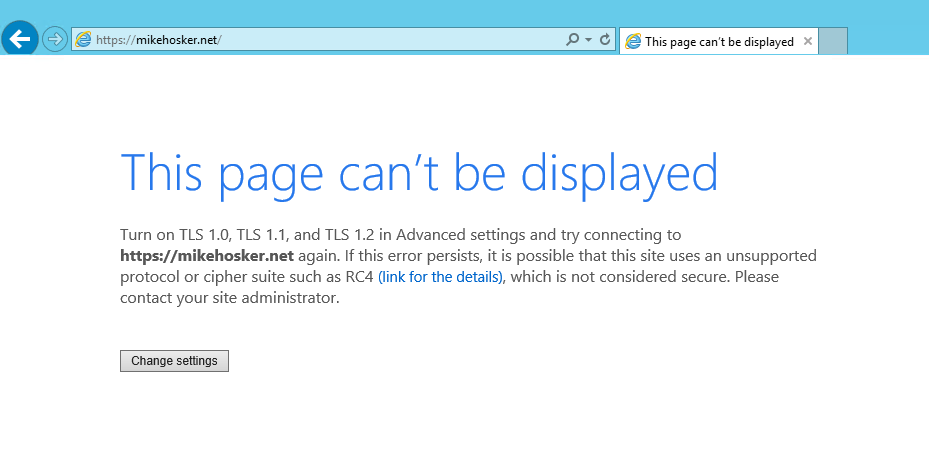
This can be caused by a range of things, including as anybody who works with Azure firewall will know – the Azure firewall block page.
So after entering some complex Azure firewall application rules I was surprised when one of the affected VMs could not access one of the whitelisted sites, namely https://portal.office.com with the TLS error being thrown!
Instinctively I looked toward the Azure firewall logs, only to see allows. So that was not the issue.
However I did recall a similar issue weeks prior where we had raised a support case with Microsoft after the Azure firewall was throwing TLS errors despite showing allows in the firewall, that case resulted in a firewall de-allocation as the solution.
What was strange this time was the fact it only affected a single machine, but it was a fresh build, so surely it couldn’t be a Windows config…
I decided to raise a ticket with the Azure firewall team who assisted with troubleshooting and analyzed network captures but concluded it was not an Azure firewall issue.
They did however pass my ticket to the Windows support team, who reached out to me and took logs. A few days later I had an email and this was the solution…
Firstly, as with all registry changes, take an export of the parent key we are going to be editing. In this case HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
Then delete the following keys –
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\ServerEnabled REG_DWORD 0x0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\ServerEnabled REG_DWORD 0x0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\ServerEnabled REG_DWORD 0x1
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\ServerEnabled REG_DWORD 0x1DisabledByDefault REG_DWORD 0x0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\ServerEnabled REG_DWORD 0x1DisabledByDefault REG_DWORD 0x0
Finally, perform a reboot on the affected machine.
And voila, access was once again restored!